Abstract
In the lead-up to the 2020 U.S. presidential election, we developed tools to monitor the follower dynamics of prominent Twitter users. This work details our investigation into several strange phenomena we observed, which suggest the presence of coordinated manipulation campaigns. We present preliminary evidence of networks of automated (bot) and potentially compromised accounts aiming to artificially inflate or diminish the perceived social status of high-profile individuals.
Key Contributions
- Novel Detection Methods: Developed monitoring tools to capture sub-second follower dynamics and identify anomalous patterns in high-profile Twitter accounts
- Comprehensive Phenomenon Documentation: Systematically catalogued four distinct types of coordinated manipulation: spikes & sawteeth, circulating accounts, resurrected ancient accounts, and follower list anomalies
- Observational Framework: Created an observational methodology designed to characterize manipulation phenomena without requiring internal platform access
- Evidence of Coordination: Provided preliminary evidence of systematic bot networks targeting prominent political figures during a critical election period
Methodological Strategy
To capture these transient phenomena, we engineered a high-frequency observational pipeline that bypassed standard sampling limitations. Our framework treated the social graph as a dynamic signal:
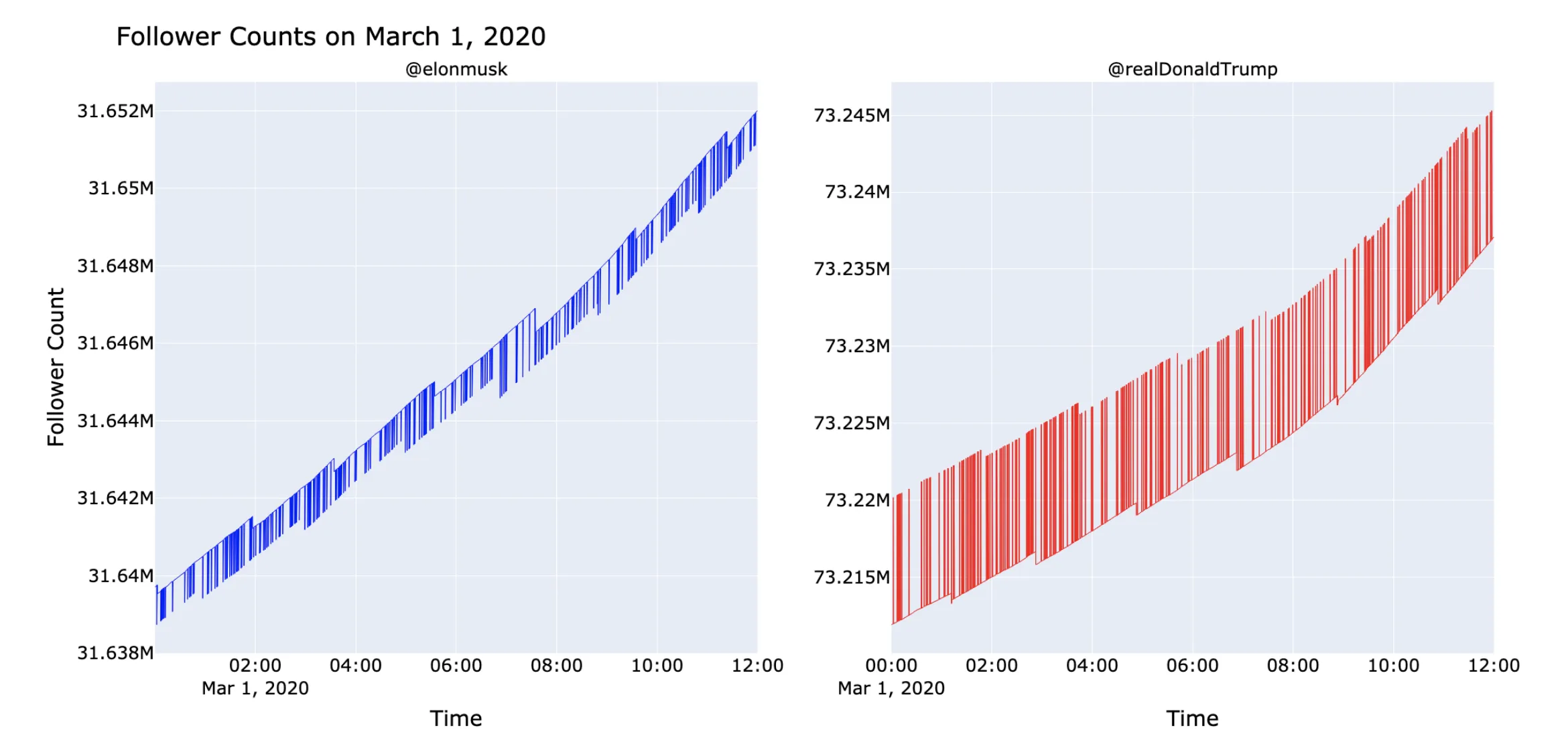
- High-Resolution Sampling: Implemented “cycling scripts” to monitor follower counts at 1-second resolution, revealing sub-minute “spike” anomalies often missed by aggregate metrics
- Recursive “Tunneling”: Developed a recursive sampling method to extract deep history from follower lists, uncovering strata of “ancient” accounts buried by recent activity
- Cross-Referencing: Correlated circulation events with follower count distortions to validate the “sawtooth” waveform hypothesis
Engineering Note: This methodology required custom infrastructure to work around Twitter API rate limits and pagination constraints. We built a distributed “tunneling” system that recursively paginated through follower lists (which Twitter caps at 5,000 per request) while respecting rate windows. The “cycling scripts” maintained persistent connections and implemented intelligent backoff strategies to sustain continuous 1-second polling over weeks of observation. This data engineering work was essential to capturing the high-resolution temporal signatures that standard API usage would miss.
Key Findings
- Spikes & Sawteeth: Dramatic, sub-second spikes and saw-tooth wave patterns in follower counts, suggesting automated activity
- Circulating Accounts: Cohorts of users repeatedly following and unfollowing the same high-profile accounts
- ‘Resurrected’ Ancient Accounts: Disproportionate numbers of pre-2010 Twitter accounts with long inactivity periods suddenly appearing as recent followers
- Follower List Anomalies: Unusual temporal groupings in follower histories suggesting historical manipulation campaigns
Significance & Sociological Impact
Beyond the technical detection of botnets, this work exposes a fundamental vulnerability in the infrastructure of modern public discourse. By targeting the metrics that algorithms use to verify relevance (such as follower counts and engagement rates) these coordinated campaigns effectively “hack” the mechanisms of social proof.
- Distortion of Democratic Signals: We argue that these inorganic behaviors are targeted attempts to manipulate the “rich-get-richer” dynamics of social platforms. By artificially inflating the status of political figures, these networks can trick recommender systems into amplifying specific narratives to legitimate users, thereby distorting the digital public square during critical election cycles.
- Platform Weaponization: The research highlights how “ancient” dormant accounts are being harvested and weaponized to bypass account-age filters, suggesting a sophisticated underground market designed to evade standard platform defenses.
- A Call for Algorithmic Transparency: Our findings suggest that reliance on raw follower metrics is increasingly dangerous. We advocate for a shift toward “verified organic engagement” metrics to prevent automated cohorts from shaping the perceived reality of millions of voters.
Citation
@article{heidenreich2020investigating,
title={Investigating Coordinated 'Social' Targeting of High-Profile Twitter Accounts},
author={Heidenreich, Hunter Scott and Mujib, Munif Ishad and Williams, Jake Ryland},
journal={arXiv},
volume={abs/2008.02874},
year={2020},
url={https://arxiv.org/abs/2008.02874},
eprint={2008.02874},
eprinttype={arXiv}
}
